security policy in network
-
Software
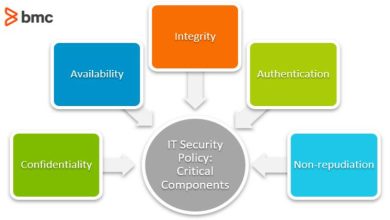
What Makes a Good Security Policy?
Information technology (IT) security is a process of securing data, people, and organizations. These measures protect against potential security breaches…
Read More »

Information technology (IT) security is a process of securing data, people, and organizations. These measures protect against potential security breaches…
Read More »