What Makes a Good Security Policy?
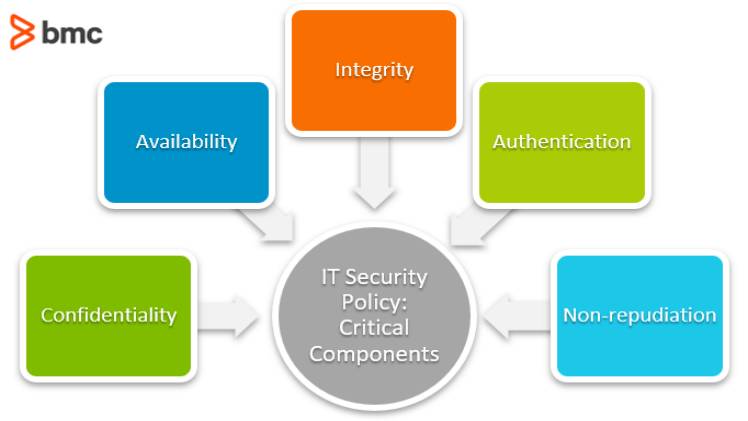
Information technology (IT) security is a process of securing data, people, and organizations. These measures protect against potential security breaches and ensure that personal information remains confidential. IT security includes many different policies, techniques, solutions, plans, actions, and devices. In addition to physical security, IT security also addresses issues related to network security, data backup, and disaster recovery. To understand what makes a good security policy, consider some of the common security problems and their solutions.
enjoy more here kannada songs download
Endpoint protection is a critical security measure for mobile devices and enterprise networks. Endpoint protection ensures that mobile devices follow security standards, alerts IT administrators of potential threats, and allows them to monitor operations and data backup strategies. Another type of security is called mobile or wireless security and encrypts data when it leaves a network. These methods are useful when employees need to access corporate applications from home or in branch offices. These types of security measures to protect sensitive data, which can make your business more profitable.enjoy new movie here 123Movies
Technical controls are important in the security process. Some security measures involve the installation of equipment to prevent unauthorized access, including password-protected systems and physical barriers.More Movies Download from here Tamilprint Those systems also include authentication solutions and intrusion protection systems. Among the many options available, security may include a combination of both. Regardless of the type of security, it is vital to consider the risk factors associated with each system, as well as the organization’s objectives. Securities are a vital part of any organization’s financial system and implementing effective controls can be both expensive and effective.more movies download jio rockers telugu